- 组件


而不是€793.50
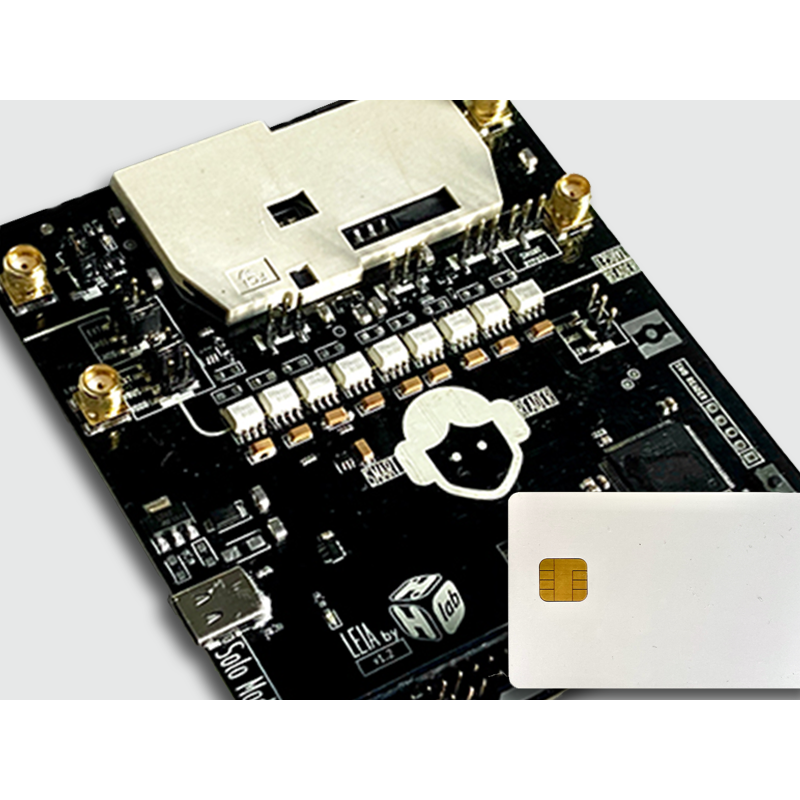
1 LEIA-SOLO Board Assembled & Tested
1 FUNCARD
This pack is composed of a LEIA-SOLO board and a FUNcard 4 smart card sample to experiment with it.
LEIA is an open hardware and open source device designed for educational, research and security assessment purposes. LEIA allows you to perform everything from side-channel analysis (SCA) and glitching attacks to full-functional smart card/USIM reading. LEIA offers a standalone mode as well as a ChipWhisperer mode. It implements a fully controlled ISO7816 stack with a dedicated custom hardware platform to acquire clean measurements for SCA characterization.
LEIA hardware comes with hands-on training tutorials that will help you to learn/teach cryptography hardening and assessment techniques on smart cad/USIM implementations.
The LEIA board is made of two main parts: a STM32 MCU that contains the firmware handling the ISO7816-3 stack, and the ISO7816-3 connector that communicates with the target smart card (i.e. handling the physical connection) and is isolated with optocouplers for clean measurements. Having a fully controlled ISO7816 stack allows to position precise triggers at dedicated events (sending an APDU, receiving the response, etc.), which helps to get synchronized traces of smart card consumption activity (and then analyze and extract secrets using classical SCA techniques). Low-level access to the ISO7816-3 protocol also allows to explore interesting paths such as smart cards conformity checks, fuzzing and so on. We have tried to bring a large coverage of the specification (T=0 and T=1, PTS negotiation, etc.).
The LEIA Firmware can be upgraded easily, without requiring a JTAG interface
All the code used for smart card communication is opensourced. This includes both the ISO7816 stack used by the LEIA Firmware and the smartleia command and control interface developed in Python.
Up to 4 trigger strategies, each one on 10 possible trigger events corresponding to classical ISO7816 events (beginning of ATR, end of ATR, sending an APDU and receiving a response, etc.).
All the code used for smartcard communication is opensourced. This includes both the Trigger strategies firmware implementation and the smartleia interface.
In both Solo and ChipWhisperer modes:
Fully integrated with PC/SC, which allows to use LEIA as a classical smart card reader.